Previous: Windows 11 | Cipher | iOS 16 iPhone
For part three we get yet another nontypical piece of evidence. Here we have a VMDK of a Windows Server environment. While the artifacts are more or less the same as Windows 10, we might find extra things of interest.
Tools used:
- Autopsy v4.20
- AXIOM v6.11
- DB Browser for SQLite v3.12.2
- FTK Imager v4.5.0.3
- KAPE v1.3.0.2
- Registry Explorer v2.0.0.0
Evidence: GCVM-MUS-001.vmdk
Maybe you can get the Team to help you Viewer this? (5 points)
What non-default remote desktop tool was installed on the system? Version number not required.
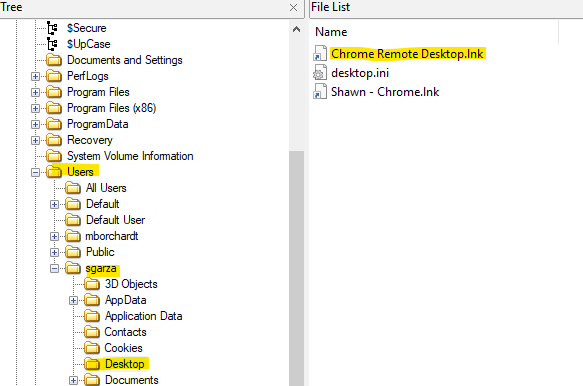
There are at least two locations you could go to find artifacts for this. One is the desktop where we can see that there was a shortcut for Chrome Remote Desktop.lnk via the "sgarza" user profile.
Figure 1: sgarza user profile desktop in FTK Imager
The other definitive location would be the Application Usage > Installed Programs section in AXIOM. Here we see that "Chrome Remote Desktop" was pulled from the user "sgarza" NTUSER.DAT registry file.
Figure 2: Chrome Remote Desktop installed in AXIOM
You could also verify by going to the source path inside the NTUSER.DAT either in AXIOM or another tool such as Registry Explorer.
Remember to turn back the clocks in November! (5 points)
What is the system timezone?
This one can be pulled quickly from AXIOM via the Operating System > Timezone Information category, which is pulling from the SYTEM registry hive.
Figure 3: Timezone details via AXIOM
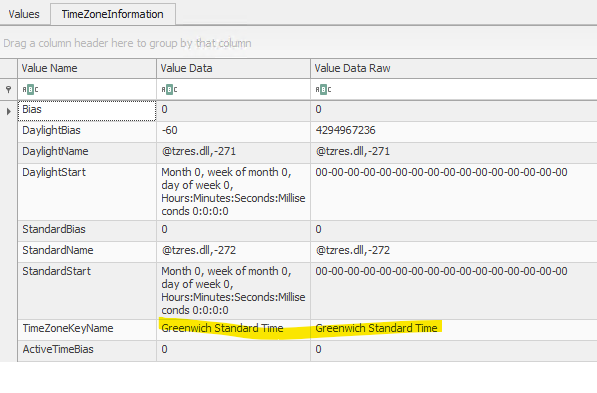
In Registry Explorer, we can use the TimeZoneInformation bookmark to see Greenwich Standard Time.
Figure 4: Timezone details via Registry Explorer from SYSTEM hive
I think I'm going to have a (National) Expresso toDay! (10 points)
What was the date and time on the system when the user account with a password hint was created? (YYYY-MM-DD HH:MM:SS)
First let's go to the Operating System > User Accounts - Windows section to see which account actually had a hint. There were only 2 user profiles (sgarza and mborchardt) but only one had a hint and that was sgarza.
Figure 5: sgarza user account profile via AXIOM
While AXIOM doesn't tell us when the user account was created in this artifact we at least know how to narrow it down. When I think of account creation I think of Windows Event Logs. These track a plethora of possible evidence including when an account was created on the system. We can do a keyword search for "sgarza" to narrow down the winevt logs. As luck would have it, the first entry that pops up is the one we're looking for.
The Event ID is 882 and the Event Record ID is 26146 where the account was created. We want the date/time which shows to be 2022-11-23 2:46:17 in proper flag format.
Figure 6: sgarza account creation via Application.evtx event log
If you needed reassurance that was correct, look back at the question title for a clue. They hint at National Expresso Day which is celebrated on November 23rd as well.
Figure 7: National Espresso Day
WHAT? I CANT HEAR YOU OVER THE FANS! (10 points)
What is the operating system edition?
Another easy one via AXIOM, hit the Operating System > Operating System Information artifact to see that the OS version was Windows Server 2019 Datacenter (1809).
You can also verify it via the SOFTWARE registry hive.
SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName
How many states did the user connect to the system from using the previously mentioned remote desktop tool?
As we've seen before utilizing previous answers or the other evidence files may help in assisting with other questions.
Which email did I use for this again? (25 points)
Not including their work account or gmail, what other email address did the primary user of the system have?
Again, looking for accounts we can pivot back to Chrome Autofill for the answer. We get emails for work (sgarza@kurvalis.com) and for personal (sgarza1284@gmail.com) but a third one from Proton Mail which was the answer, "sgarza1284@proton.me".
Figure 10: Chrome Autofill emails via AXIOM
Chrome Autofill resides at:
C:\Users\sgarza\AppData\Local\Google\Chrome\User Data\Default\Web Data
Opening in DB Browser for SQLite we can go to the "autofill" table and see the same results:
What is the name for the bookmark item added on December 11, 2022 at 2:04:54 AM (local system time)?
C:\Users\sgarza\AppData\Local\Google\Chrome\User Data\Default\Bookmarks
I'm not sure if AXIOM parses synced bookmarks (it appears it doesn't at least for folders) so we can just go to the file directly and view it since it's just JSON formatted. There is a little section at the bottom that shows a key of "synced" with one entry, which was a folder.
What was the second domain in the search list provided by the DHCP server?
I honestly had no idea where DHCP server lists resided so I took to Google for clues. I came across a blog post from Forensafe that has a great list of artifacts pulled from the registry. They said to check the following path:
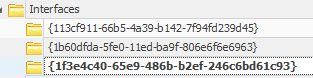
SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces
Inside are three folders:
Figure 13: Interfaces via Registry Explorer
The first two didn't have much but the third had a lot of more values. One value is "DhcpDomainSearchList" which seemed to directly correlate to our question. Inside was 3 different domains separated by commas, the second of which was "c.boxwood-scope-369502.internal".
What is the GUID of the PowerShell module found on the system?
So we get two clues, Google Cloud and Powershell, where do we start? I did two separate keyword searches for "Google" and "Cloud" in AXIOM to see what popped up. I saw we had Google Cloud SDK installed on the computer and the file system folder was located at:
C:\Program Files (x86)\Google\Cloud SDK
When all else fails dig into the folder structure and see what comes about. Sure enough, I came across as .ps1 file which is commonly associated with PowerShell.
C:\Program Files (x86)\Google\Cloud SDK\google-cloud-sdk\platform\GoogleCloudPowerShell\GoogleCloud.psd1