Previous: Marsha's PC | Beth's iPhone | Marsha's iPhone
The return to Heisenberg's Samsung was much welcomed after struggling mightily with Marsha's PC. Let's see what his phone had to offer.
#13 optimize 📦
What package was used by the Mobile App used by Heisenberg to scan/optimize his device? (package name)
From what I recall I fumbled around the Installed Apps (Vending) report in ALEAPP and looked at the titles of the applications. Device Care seemed to fit so I looked it up on the Play Store and saw some screenshots of optimization so I tried the package com.samsung.android.lool and it worked.
Figure 1: Device Care on the Play Store
#14 🚘lookup
What is the package name used by the Mobile App which Heisenberg looked up license plates/VIN of target vehicles?
I took a quick peek at the Installed Apps (Vending) report in ALEAPP to see what applications were installed. There were a few that dealt with cars but only one glaring one, com.orto.usa.
Figure 2: Installed apps in ALEAPP
#15 📱ZBDDB
What app does "zebedee.db" correspond to?
A quick search in Cellebrite Physical Analyzer gave me the path to the database we are looking for. I had noticed that database was found in the folder with the package name "com.google.android.apps.turbo" which I'm all too familiar with. The app in question is Device Health Services which I've done some research on.
Figure 3: zebedee.db file location
#16 🔑📶
What is the password for mobile data hotspot on Heisenberg's device that was shared with Beth? (Case Sensitive)
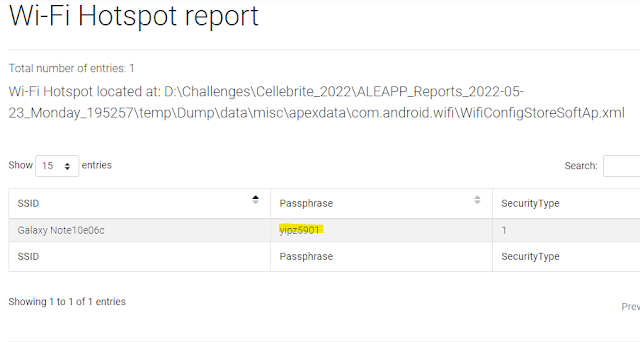
Another easy one provided by ALEAPP. Heading down to the Wi-Fi hotspot report you can see the password/passphrase was "yipz5901".
Figure 4: Wi-fi hotspot password in ALEAPP
This can be pulled from the file at the path:
data/misc/apexdata/com.android.wifi/WifiConfigStoreSoftAp.xml
#17 🔵🦷MAC
What is the Bluetooth MAC address, date, and time for the last connection to Bose Sound Touch/CE2D10 (MAC YYYY-MM-DD HH:MM:SS) (24-hr format) Example: aa:bb:cc:dd:ee:ff 2020-04-28 18:29:33
The keyword here is "last connection". I thought that to be odd as the normal bluetooth location will show first connected timestamp. From the Bluetooth Connections report in ALEAPP there were 3 different devices, one of which is the Bose item in question.
Figure 5: Bluetooth connections report in ALEAPP
I did a quick keyword search on the MAC address in Physical Analyzer, resulting in some hits in another database file under the
SmartThings application. Inside the QcDb.db database there is a "devices" table that has a timestamp, which was later than the first connect timestamp.
Figure 6: QcDb.db > devices table in PA
Converting it from Epoch we get it as 6/27/2021 5:47:41 PM. With proper formatting, we get the answer of 2c:6b:7d:1d:21:a7 2021-06-27 17:47:41.
#18 ☎number
What is the phone number of the undercover cop who approached Heisenberg? (Format: +1-212-555-1234)
First thing I checked out was the SMS/MMS database at:
data/data/com.android.providers.telephony/databases/mmssms.db
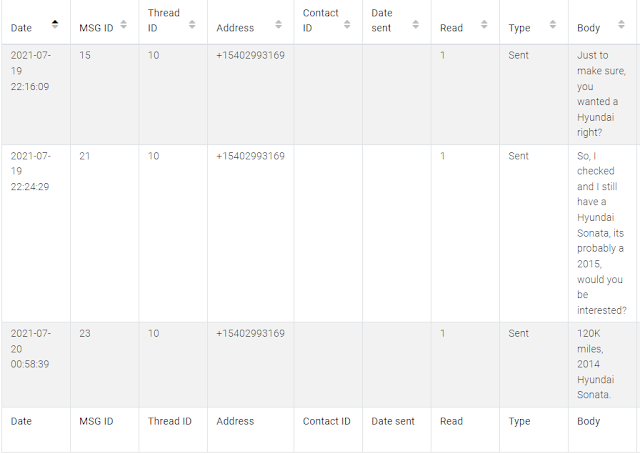
From there I just did a quick filter for Hyundai (the first hint) which gave results instantly in ALEAPP.
Figure 7: SMS filtered in ALEAPP
We can see all messages lead to the number +1-540-299-3169.
#19 🆓
BONUS Question Select anything to receive 10pts.
Free points is always nice, you can't go wrong!
#20 💌
What is the total number of messages deleted (could be partially or not recovered)?
This answer was pulled directly from Physical Analyzer. If you look at the Messages category you can see that 4 items were deleted (in red).
Figure 8: Deleted Messages in Physical Analyzer
#21 📱📶WV
Based on retrieved data from the device, the phone operated in West Virginia. True/False?
Honestly I took a wild guess on this, not sure why there were 3 chances to get this right, so I guessed True which was correct.
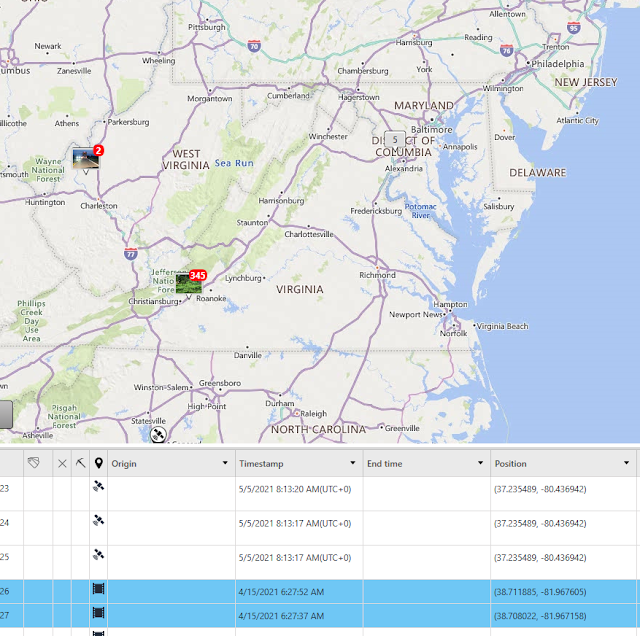
We can dig into this further through Physical Analyzer using the parsed Device Locations. There were 2 photos that were taken in West Virginia on 4/15/2021. Coordinates place it around 2244-2232 Kanawha Valley Rd, Southside, WV 25187 address.
Figure 9: Device Locations in Physical Analyzer
#22 🌐📷
How many native images on the device contain location data?
This was another question that I'm pretty sure I got correct but got locked out of and then later on reimbursed points so I don't know the true answer they were looking for. My interpretation of the question was that they were looking for photos that were taken with the phone that contained EXIF location data. So I first opened the Images and filtered on only images found in the DCIM folder which gave me a subset of 76 images. I then used the metadata with location filter to reduce it even further to 52 images.
Figure 10: DCIM photos with location metadata
#23 Device ℹ
What is the IMSI of the device?
ALEAPP pulls this out quick for us. On the Case Information > Device details tab we see the IMSI was 310260275793897. The checkin.xml file also holds this information at the path:
data/data/com.google.android.gms/shared_prefs/Checkin.xml
Figure 11: Checkin.xml with the last SIM details
#24 ㊙ app
Was the image with the MD5 hash "066858f4b1971b0501b9a06296936a34" hidden by Heisenberg? If Yes, what is the name of the package of the app used to hide the image else answer No. Example: yes+com.apple.wallet
A search in Physical Analyzer for the hash yielded a few images all which were the exact same. The image was hidden inside the com.flatfish.cal.privacy app which is called was formerly a Calculator hiding app (no longer on the Play Store). So the proper formatted answer was "yes+com.flatfish.cal.privacy".
Figure 12: Photo hidden in com.flatfish.cal.privacy
#25 #️⃣tag
What is the name, username and account number corresponding to the media id "2623237359273252101". Was Heisenberg following this account? (Answer Format: Name_Username_AccountNumber_Yes/No) (No Spaces)
A deep hex search for the media ID led me to a -wal file inside the Instagram databases folder.
data/data/com.instagram.android/databases/user_reel_medias_room_db_46770300793-wal
We can export out the main database along with the -wal to properly open it inside DB Browser. In the "user_reel_medias" table we can filter on the "media_ids" column with the ID we were provided to see the entry. In the "data" column we can copy out the JSON information to NotePad++ for easier reading.
Starting in row 23 we start to see user information related to the post. We can see the username was "marsha4mellos" and the full name was "Marsha Mellos".
Figure 13: Instagram Reel user info
A little further down in the "friendship_status" section we can see that the "following" key was listed with a value as True.
Figure 14: Instagram Reel relationship status
Putting this all together in the proper answer format, we get "MarshaMellos_marsha4mellos_44072330861_Yes".
#26 ⌚stamp
What is the Date and Time for the last use of Instagram on Heisenberg's device? (YYYY-MM-DD HH:MM:SS) (24-hr format) example: 2019-03-22 23:45:12
In keeping with the Instagram databases I did a little digging and found one that seemed to fit the mold of the question:
data/data/com.instagram.android/databases/time_in_app_46770300793.db
In the "intervals" table we see start and end times of usage in Unix Epoch milliseconds format.
Figure 15: Instagram usage timestamps
Converting to normal date/time format we see the last use of Instagram ended on 2021-07-22 19:06:37.
#27 🔥card
Find the first six and the last four digits of a burner card that was used by Heisenberg for gas. (FirstSix_LastFour)
Looking at the Install Applications I filtered for "gas" and had one hit for an application called GetUpside, package named com.upside.consumer.android. Navigating to the application folder I came across a realm database file of interest.
data/data/com.upside.consumer.android/files/upside.realm
I'm glad Physical Analyzer has a format viewer for this because it can be a bear. In the "class_CreditCard" field we hit the motherload. There were the two keys right in front of us that give the answer, "firstSix" and "lastFour". We can see the Visa card used "414720_0834".
Figure 16: Upside credit card numbers
#28 🏙🤝🏻
Heisenberg intended to have a meeting with the person he was intensely communicating with. Establish the name of the street in which the meeting was about to take place and the exact time of the chat in which the requesting party confirmed the meeting. format: [street name] [time HH:MM:SS UTC] example: Main St. 19:27:21
This was the one question that I had no idea what the real answer was. I found some messages between Heisenberg and Beth through Instagram that appeared to show a meetup at the Vienna Inn in Vienna, Virginia.
There were also conversations through native messages that had Heisenberg meeting with an undercover cop near the Washington Street Tennis Courts in Blacksburg, Virginia.
I tried both street addresses with the times as well but I could have had the wrong combination as the "requesting party" timestamp is unclear if that meant Heisenberg or the other person he was communicating with.
#29 🌎location
This meeting was a setup in which a police agent arrested Heisenberg. Find evidence that was generated during the estimated time of the meeting in which you can witness (see and hear) Heisenberg’s arrest. What is the location in which this evidence was created? Note: There are only two instances of similar evidence that has geographical locations. format: Lat,Long example: 33.333,-77.7777
Since I played the 2021 version of the CTF, I know that there was a video of his arrest by an undercover cop. Quickly going through his DCIM folder for videos I came across the only one at the path:
data/media/0/DCIM/Camera/20210720_150222.mp4
Oddly enough, for some reason Physical Analyzer couldn't detect the lat/long of the video so I dumped it out to my desktop and opened it with Exiftool which detected it properly. EXIF data places the video at 37.2249,-80.4159. I'm wondering if it's because it wasn't the exact embedded coordinates it was looking for.
Figure 17: Exif lat/long of the 20210720_150222.mp4