It's that time of year again, and the Magnet Virtual Summit closed out last week (check out the replays). As part of the summit we got another fantastic virtual CTF from Jessica Hyde and the wonderful students from Champlain College. Lets kick things off by diving into the Egg Hunt!
Boxed Crazy Bread
What is the flag found in the message below:
CGTAOYFNHGHLIMGORUTNOODEGEAS0UNALISUUTETFGAN5
As always, the question title gives some hints of where to start. Using the dcode.fr identifier we see some suggestions but the one we are looking for is a bit down the list. Little Caesar's does have good breadsticks.
Figure 1: dcode.fr identifier
Utilizing the Caesar Box Cipher we get the proper results, showing the flag was "AM0NGU5".
Figure 2: Caesar Box cipher decoder
More bits please!
Using the keyword MAGNETVUS, what is the flag found in the message below:
55828323131891953189327594652829164582918353894339858568943391314972393439294341718944
Once again the title is key to finding results. The cipher identifier shows that it's a Morbit Cipher. Using the specified decoder and including the keyword supplied, we get the flag. The answer was "WH3AT5".
Figure 3: Morbit cipher decoder
Skip to My Lou
What is the flag found in the message below: 1A3HCCN
I tried the cipher identifier but it didn't bring any obvious leads to what type we needed so I ended up doing a quick Google search for "skip cipher" and it let me right back to dcode.fr's own. We see the answer was "1CHANC3".
Figure 4: Skip cipher decoder
OMG They Killed Me
We are given the QR code from above, if you can it (using a phone or other methods) you get the following text results:
Mmfppfpppmfmpffmmmfmpfmfpmfmmmfmpmffppfpppfmm ffmppffmf mpfppffmfpppmpm fmpmfpmpp mppmfmmfm Fmpmfpmpp mpfpmfmmmmfm mfffmm mfm1mmmpppfmppffmmmfmp
Looking at the title again for clues, I'm not a South Park fan but I know that familiar phrase. Of course dcode.fr has a decoder called Kenny Language. We get the flag of "g1antrat".
What is the flag found in the message below:
.y1f07318438d1u0h5338474h7y4w0n51323h7n0c4851941f3h7n01741v4f05w41nw0nk114079n1d20cc4
I could tell right off the jump that this was reversed by the period at the front (as well as the mirror clue). Reversing the text in dcode.fr we get the following:
4cc02d1n970411kn0wn14w50f4v14710n7h3f1491584c0n7h32315n0w4y7h4748335h0u1d83481370f1y.
Figure 6: Text reverser
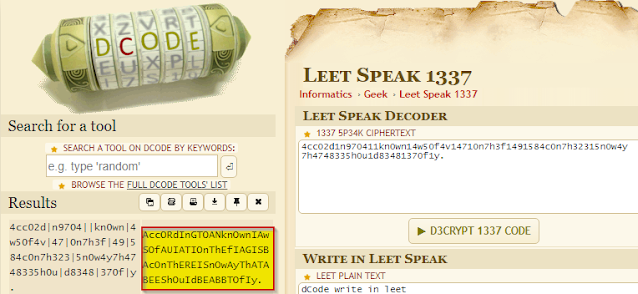
You can vaguely make out words from it now but vowels appear to be replaced with numbers. Having seen this type of language many times I knew it was some form of L33T speak, and of course dcode.fr has a decoder.
Figure 7: Leet Speak decoder
Reading through the formatting a bit (sorry it gets cut off), we see the flag was "BAc0N".






%20Online%20Right%20to%20Left%20Writing%20-%20Reverse%20Order.png)