Previous: Egg Hunt
If anything the iOS section of the Magnet CTF proved to me, you really need to deep dive into the database files to pull out all the information. I think it was fantastic how they made you go outside the box to find flags in this section.
iOS Device
Account Scout (5)
What's the Apple ID email associated with this deviceFlag should look like: flag<sally@mail.com> (Don't include flag<>)
Parsing through using iLEAPP we can see
What's in the toolbox? (5)
What tool was used to perform the acquisition on this device? Note: You only have 1 attemptThere was a MEAT.log in the evidence folder so naturally Jack Farley used his own tool for the acquisition!
Mobile Evidence Acquisition Toolkit
I would walk 3,264 miles just to hack you tonight (10)
What is the name of this user's favorite city in Apple Maps?
There weren’t many Apple Maps coordinates that were parsed out outside of the Burlington, Vermont
area and outside of the normal dates. Because of the hint in the title, we see one entry for London.
The name stuck out to me as something the creator would highlight, and it worked. Loserville
What medication is this user currently on?
Medical information is stored as part of the Health app on an iPhone at the following path:
The file is a plist which can be parsed.

Medical information is stored as part of the Health app on an iPhone at the following path:
/iOS_Filesystem/private/var/mobile/Library/MedicalID/MedicalIDData.archive
The file is a plist which can be parsed.
We we the user has some medication listed, Lysergic acid diethylamide.
Who am I? (10)
Who am I? (10)
What's the name of this device?
This can be pulled from:
iLEAPP parses it quickly, “Alan's Fantastical iPhone”

Ye ole 9 to 5 (10)
This can be pulled from:
/iOS_Filesystem/private/var/root/Library/Lockdown/data_ark.plist
iLEAPP parses it quickly, “Alan's Fantastical iPhone”
Ye ole 9 to 5 (10)
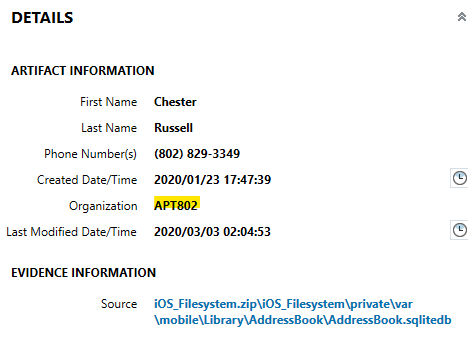
What is the company associated with the contact "Chester Russell"?
AXIOM parses this out quickly from Contact Info. We can see Chester is associated with APT802.
Back in my day we weren't glued to our phones (25)
AXIOM parses this out quickly from Contact Info. We can see Chester is associated with APT802.
Back in my day we weren't glued to our phones (25)
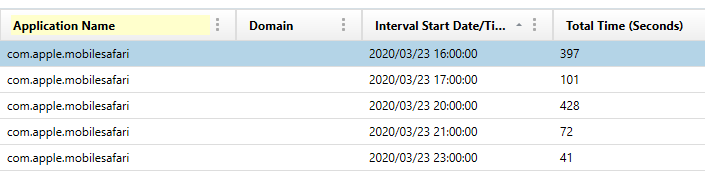
How many seconds did the user have Safari open between the hours of 12:00:00 and 20:00:00 on March 23rd, 2020?
Only enter the number
We can calculate a sum of screen time application usage and filtering on Safari. Once we add up the
seconds column, we get a total time of 1039 seconds.
Creeper aw man (25)
Only enter the number
We can calculate a sum of screen time application usage and filtering on Safari. Once we add up the
seconds column, we get a total time of 1039 seconds.
Creeper aw man (25)
Looks like a MineCraft server was hosted on this device?? Find the username of a player who has joined
I did a quick keyword search on “Creeper” which brought back some text files which appear to be text splash sayings:
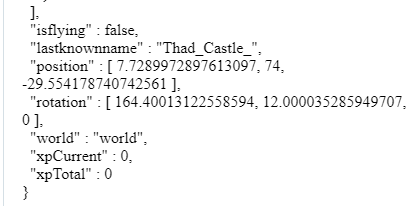
I went to the location and up a few folders to find the “players” folder which had a JSON file inside:
Near the bottom we can see the flag, the username Thad_Castle_
Hackerman (25)
What is the first IP address that this user targeted via a popular hacking tool?
As I assumed the iPhone was jailbroken from other questions, I found remnants of information related to the Metasploit framework. In traversing the iOS filesystem, we can see a bash history file at the following path:
Inside the plaintext file shows two different IP addresses that were targeted, but the first was 184.171.152.175.

Near Flag Communication (25)
I did a quick keyword search on “Creeper” which brought back some text files which appear to be text splash sayings:
\usr\dev\cuberite.tar.gz\cuberite\Server\Plugins\NetworkTest\splashes.txt
I went to the location and up a few folders to find the “players” folder which had a JSON file inside:
\usr\dev\cuberite\Server\players\67\451c08-f6c8-436a-ba16-7eee924e3bd0.json
Near the bottom we can see the flag, the username Thad_Castle_
Hackerman (25)
What is the first IP address that this user targeted via a popular hacking tool?
As I assumed the iPhone was jailbroken from other questions, I found remnants of information related to the Metasploit framework. In traversing the iOS filesystem, we can see a bash history file at the following path:
iOS_Filesystem/private/var/mobile/.msf4/history
Inside the plaintext file shows two different IP addresses that were targeted, but the first was 184.171.152.175.

Near Flag Communication (25)
What is the Tag ID of the scanned NFC tag? Remember MC questions have a 1 attempt limit

I assume this temp storage stored some connection info at one time, I'm not sure if there is an easier way to find this answer elsewhere.
Check out my Spotify (50)
This user's Spotify playlist is looking a bit suspicious..?
A quick keyword search for “playlist” shows Chester and Alan exchanged Twitter DM’s. The playlist can be found at https://t.co/0Qc9pWfe5x

The flag is Destroy Education Debt.
Plug it in plug it innnn (50)
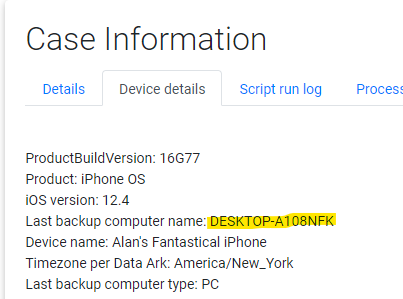
What is the name of the computer that was used to sync with this device?
Good ole iLEAPP pulls this out right from the Data Ark:
On the main page of the report we can see it connected to DESKTOP-A108NFK:
SNAP.. That's going int my cringe compilation (50)
How many applications have iOS Snapshots?
Application Usage info can be pulled from the database at the following path:
In the kvs_debug table we can filter the key down to XBApplicationSnapshotManifest resulting in 88 apps, the flag.

Spraaang Breaaaak (50)
How many guests were registered in the trip to Disney?
Warning: You only have 3 attempts at this
To start, let’s look at the installed applications:
We see multiple Disney applications but MyDisneyExperience is what we want to deep dive into. From the mobile_installation log we can see the following path contains app information:

Sifting through files, we can see an Itinerary DB file in the Library folder of the application path above.
Opening the database with DB Browser for SQLite, there is 4 tables with one of importance:

Exporting the BLOB to a plist, we can open that in an editor and see the answer for the question, 6 adults.

Thank you to evandrix for some hints post CTF on a few of these.
- 377EE22E104347
- AD2A7A3E3C63F7
- 96C8E50757329E
- E5DB5FE6A6984D
- 041146220F5E80
- 2D52E5017D690E
- 64DCD00FD51BFB
- 64DCD00FD51B03
- 925F65AC9786B6
/iOS_Filesystem/private/var/tmp/syslog

I assume this temp storage stored some connection info at one time, I'm not sure if there is an easier way to find this answer elsewhere.
Check out my Spotify (50)
This user's Spotify playlist is looking a bit suspicious..?
A quick keyword search for “playlist” shows Chester and Alan exchanged Twitter DM’s. The playlist can be found at https://t.co/0Qc9pWfe5x
The flag is Destroy Education Debt.
Plug it in plug it innnn (50)
What is the name of the computer that was used to sync with this device?
Good ole iLEAPP pulls this out right from the Data Ark:
/iOS_Filesystem/private/var/root/Library/Lockdown/data_ark.plist
On the main page of the report we can see it connected to DESKTOP-A108NFK:
SNAP.. That's going int my cringe compilation (50)
How many applications have iOS Snapshots?
Application Usage info can be pulled from the database at the following path:
/iOS_Filesystem/private/var/mobile/Library/FrontBoard/applicationstate.db
In the kvs_debug table we can filter the key down to XBApplicationSnapshotManifest resulting in 88 apps, the flag.

How many guests were registered in the trip to Disney?
Warning: You only have 3 attempts at this
To start, let’s look at the installed applications:
We see multiple Disney applications but MyDisneyExperience is what we want to deep dive into. From the mobile_installation log we can see the following path contains app information:
Sifting through files, we can see an Itinerary DB file in the Library folder of the application path above.
Opening the database with DB Browser for SQLite, there is 4 tables with one of importance:

Exporting the BLOB to a plist, we can open that in an editor and see the answer for the question, 6 adults.

Thank you to evandrix for some hints post CTF on a few of these.

